Privacy
 www.privacyguides.org
www.privacyguides.org
After [almost 2 years](https://github.com/privacyguides/privacyguides.org/issues/1899), Privacy Guides has added a new [Hardware Recommendations](https://www.privacyguides.org/en/basics/hardware/) section to their website. Thanks to [Daniel Nathan Gray](https://github.com/dngray) and [others](https://github.com/privacyguides/privacyguides.org/pull/2268) for implementing this new hardware guide
ISPs are forced to block DNS request to certain hosts, they also monitor your DNS requests, and sometimes aren't updated that or are slow. Which DNS servers do you use or would recommend to others?
I'm getting IP-banned using yt-dlp. It seems that this is a [known issue](https://github.com/yt-dlp/yt-dlp/issues/10128). Have any of you run into this, and if so, what has been your solution? I currently use a VPN via a VPS. I am able to view youtube via the web client and use youtube-dl without VPN, but I am only unable to get through using the CLI on the VPN. I have also tried fiddling with some CLI args (like `--extractor-args "youtube:player_client=web"`) but that is also unsuccessful. My next step is to try signing up for mullvad to see if I can get around it that way, but would like to hear if this is affecting existing mullvad users. Open to hearing other solutions as well. Thanks!
 www.buskill.in
www.buskill.in
We're happy to announce that [BusKill is presenting at DEF CON 32](https://www.buskill.in/defcon32/). **What: Open Hardware Design for BusKill Cord When: 2024-08-10 12:00 - 13:45 Where: W303 – Third Floor – LVCC West Hall** | [](https://www.buskill.in/defcon32/) | |:--:| | [BusKill is presenting at DEF CON 32](https://www.buskill.in/defcon32/) | via [@Goldfishlaser@lemmy.ml](https://lemmy.ml/u/Goldfishlaser) # What is BusKill? BusKill is a laptop kill-cord. It's a USB cable with a magnetic breakaway that you attach to your body and connect to your computer. | [](https://www.buskill.in/#demo) | |:--:| | *Watch the [BusKill Explainer Video](https://www.buskill.in/#demo) for more info [youtube.com/v/qPwyoD_cQR4](https://www.youtube.com/v/qPwyoD_cQR4)* | If the connection between you to your computer is severed, then your device will lock, shutdown, or shred its encryption keys -- thus keeping your encrypted data safe from thieves that steal your device. # What is DEF CON? DEF CON is a yearly hacker conference in Las Vegas, USA. | [](https://www.buskill.in/defcon32/) | |:--:| | *Watch the [DEF CON Documentary](https://www.youtube.com/watch?v=3ctQOmjQyYg) for more info [youtube.com/watch?v=3ctQOmjQyYg](https://www.youtube.com/watch?v=3ctQOmjQyYg)* | # What is BusKill presenting at DEF CON? I ([goldfishlaser](https://github.com/goldfishlaser)) will be presenting **Open Hardware Design for BusKill Cord** in a Demo Lab at DEF CON 32. **What: Open Hardware Design for BusKill Cord When: Sat Aug 10 12PM – 1:45PM Where: W303 – Third Floor – LVCC West Hall** Who: Melanie Allen ([goldfishlaser](https://github.com/goldfishlaser)) [More info](https://forum.defcon.org/node/249627) ## Talk Description BusKill is a Dead Man Switch triggered when a magnetic breakaway is tripped, severing a USB connection. I’ve written OpenSCAD code that creates a 3D printable file for plastic parts needed to create the magnetic breakaway. Should anyone need to adjust this design for variations of components, the code is parameterized allowing for easy customization. To assemble a BusKill Dead Man Switch cord you will need: 1. a usb-a extension cord, 2. a usb hard drive capable of being attached to a carabiner, 3. a carabiner, 4. the plastic pieces in this file, 5. a usb female port, 6. a usb male, 7. 4 magnets, 8. 4 pogo pins, 9. 4 pogo receptors, 10. wire, 11. 8 screws, 12. and BusKill software. | [](https://www.buskill.in/defcon32/) | |:--:| | Golden DIY BusKill Print | Full BOM, glossary, and assembly instructions are included in the [github repository](https://github.com/BusKill/usb-a-magnetic-breakaway). The room holds approx. 70 attendees seated. I’ll be delivering 3 x 30 min presentations – with some tailoring to what sort of audience I get each time. ## Meet Me @ DEF CON If you'd like to find me and chat, I'm also planning to attend: - ATL Meetup (DCG Atlanta Friday: 16:00 – 19:00 \| 236), - Hacker Kareoke (Friday and Sat 20:00-21:00 \| 222), - Goth Night (Friday: 21:00 – 02:00 \| 322-324), - QueerCon Mixer (Saturday: 16:00-18:00 \| Chillout 2), - EFF Trivia (Saturday: 17:30-21:30 \| 307-308), and - Jack Rysider’s Masquerade (Saturday: 21:00 – 01:00 \| 325-327) I hope to print many fun trinkets for my new friends, including some BusKill keychains. | [](https://www.buskill.in/defcon32/) | |:--:| | Come to my presentation @ DEF CON for some free BusKill swag | By attending DEF CON, I hope to make connections and find collaborators. I hope during the demo labs to find people who will bring fresh ideas to the project to make it more effective.
I self host a bunch of things on my home network and since i dont have a static ip i use duckdns so i can access it via the greater web and set up ssl etc. Works great for my laptop and other people but on my phone where im using rethink dns to filter web access the duckdns domain doeant resolve (its not getting blocked it just not resolving at all). It resolves on cloudflare and ive set that as the fallback for rethink but still doesnt resolve any advice/help would be greatly appreciated.
I have a bunch of hard disks that have come to the end of their useful life, I was thinking about physically destroying them, but that seems like a lot of work. https://github.com/martijnvanbrummelen/nwipe Nwipe and shreados are very popular. What are your thoughts on the effectiveness of nwipe?
chat.positive-intentions.com github.com/positive-intentions/chat I'm excited to share with you an instant messaging application I've been working on that might interest you. This is a chat app designed to work within your browser, with a focus on browser-based security and decentralization. What makes this app unique is that it doesn't rely on messaging servers to function. Instead, it works based on your browser's javascript capabilities. Here are some features of the app: - Encrypted messaging: Your messages are encrypted, making them more secure. - File sharing: Easily share files using WebRTC technology and QR codes. - Voice and video calls: Connect with others through voice and video calls. - Shared virtual space: Explore a shared mixed-reality space. - Image board: Browse and share images in a scrollable format. Your security is a top priority. Here's how the app keeps you safe: - Decentralized authentication: No central server is required for login, making it harder for anyone to gain unauthorized access. - Unique IDs: Your ID is cryptographically random, adding an extra layer of security. - End-to-end encryption: Your messages are encrypted from your device to the recipient's device, ensuring only you and the recipient can read them. - Local data storage: Your data is stored only on your device, not on any external servers. - Self-hostable: You have the option to host the app on your own server if you prefer. A decentralized infrastructure has many unique challenges and this is a unique approach. Ive taken previous feedback and made updates. Its important to note, the app is an unstable proof-of-concept and a work-in-progress. Its important to understand at this early stage in the project, there will be breaking changes. It is not ready to replace any existing apps or services. While the app is aiming to be an encrypted and secure chat system, the project is not mature enough to have been reviewed by security professionals and should not be considered encrypted or secure. it is provided for testing/review/feedback purposes. Looking forward to hearing your thoughts! [The live app](https://chat.positive-intentions.com) [About the app](https://medium.com/@positive.intentions.com/introducing-decentralized-chat-377c4aa37978) [Even more about the app](https://medium.com/@positive.intentions.com/our-decentralized-microfrontend-architecture-61bb8f1576f0) [Docs](https://positive-intentions.com) [Subreddit](https://www.reddit.com/r/positive_intentions/)
https://www.apple.com/newsroom/2024/05/apple-and-google-deliver-support-for-unwanted-tracking-alerts-in-ios-and-android/
 tuta.com
tuta.com
cross-posted from: https://lemmy.world/post/10958052 > Vanguard, the controversial anti-cheat software initially attached to Valorant, is now also coming to League of Legends. > > Summary: > > The article discusses Riot Games' requirement for players to install their Vanguard anti-cheat software, which runs at the kernel level, in order to play their games such as League of Legends and Valorant. The software aims to combat cheating by scanning for known vulnerabilities and blocking them, as well as monitoring for suspicious activity while the game is being played. However, the use of kernel-level software raises concerns about privacy and security, as it grants the company complete access to users' devices. > > The article highlights that Riot Games is owned by Tencent, a Chinese tech giant that has been involved in censorship and surveillance activities in China. This raises concerns that Vanguard could potentially be used for similar purposes, such as monitoring players' activity and restricting free speech in-game. > > Ultimately, the decision to install Vanguard rests with players, but the article urges caution and encourages players to consider the potential risks and implications before doing so.
 video.lqdn.fr
video.lqdn.fr
Fighting against surveillance has never been easy. But in the past year it has been specially tough in France. This talk is about shedding light on the many situations where the French State used surveillance to increase repression, mainly against activists, during the last months. Not to despair of this, but willing to provide a sincere overview to the rest of the world, La Quadrature du Net proposes to depict this situation as a satirical tale, with its own characters, plots and suspense. We want to show the political tension going on right now in France and how the checks and balances are lacking to stop this headlong rush to a surveillance state. Looking back to France in 2023, what do we see? Implementation of new technologies such as drones, DNA marking or new generation of spywares. Also, an intensification of political surveillance, either by law enforcement deploying disproportionate means of investigations towards environmental activists or intelligence services using cameras or GPS beacons to spy on places or people that they find too radical. It was also the year of the “8 December” case, a judicial case where among other things, encrypted communications of the prosecuted persons were considered as signs of "clandestinity" that reveal criminal intentions. On top of this, we also had to deal with the legalization of biometric surveillance for the Olympics and massive censorship of social networks when riots erupted in suburbs against police violence. This talk is about showing the reality of the situation at stake right now in France, and how it could influence the rest of Europe. At the end, we hope to raise awareness in the international community and start thinking about how, together, we can put pressure on a country who uses its old reputation to pretend to be respectful of human rights. Source: https://media.ccc.de/v/37c3-12309-a_year_of_surveillance_in_france_a_short_satirical_tale_by_la_quadrature_du_net French version: https://video.lqdn.fr/w/rXmBKD6NcfxWxJEPHUZc4Z German version: https://video.lqdn.fr/w/315ZAQFMTMG7wqiMDdGvsi
 www.bbc.co.uk
www.bbc.co.uk
cross-posted from: https://links.hackliberty.org/post/609883 > This BBC interview has a #Cloudflare rep David Bellson who describes CF’s observations on internet traffic. CF tracks for example the popularity of Facebook vs. Tiktok. Neither of those services are Cloudflared, so how is CF tracking this? Apparently they are snooping on traffic that traverses their servers to record what people are talking about. Or is there a more legit way Cloudflare could be monitoring this activity?
This guide isn't a "what not to buy" list. It acknowledges that no internet-connected toy can be entirely child proof because tech companies have yet to prioritize children's safety in their designs.
Some banks will annually mail a paper “welcome” letter to all customers purely for the purpose of collecting bounced mail ultimately to verify if anyone has moved without telling them. The letters never state that’s the purpose.. they take that opportunity to talk about their service in arbitrary ways. Some banks even charge customers a fee for their cost in doing that. If you ask the banker about it they readily admit that it’s an address verification technique. That’s it.. just a PSA so folks are aware, as it is a bit sneaky. Some national postal services (e.g. USPS) sell your mail forwarding information which is how you get tracked to your new location by various entities even when you did not inform them of your new address. So obviously a good defensive measure is to never use the mail forwarding service. Select the entities you want to know your new address and inform them directly. But then to get some immunity to the sneaky trick in the 1st paragraph, perhaps give the next resident a stack of addressed envelopes and stamps and ask the next resident to ~~forward~~ (remail) for you.. or just ask them to trash your mail instead of returning it.
 arstechnica.com
arstechnica.com
Tech legal expert Eric Goldman wrote that a victory for the plaintiff could be considered "a dangerous ruling for the spy cam industry and for Amazon," because "the court’s analysis could indicate that all surreptitious hook cameras are categorically illegal to sell." That could prevent completely legal uses of cameras designed to look like clothes hooks, Goldman wrote, such as hypothetical in-home surveillance uses.
Chat Control, the new EU law project to weaken messaging systems and get rid of E2E encryptions so as to scan in clients sides the content of the messages (but only for children safety, of course).
 www.politico.eu
www.politico.eu
After the Tchap project based on Matrix, the French Prime Minister asks anyone in the gouvernement to use Olvid, the only app validated by the ANSSI, with metadata encryption and no centralised architecture nor contacts discovery. But only the front-ends are open source, not the back-end. Source: https://www.politico.eu/article/france-requires-ministers-to-swap-whatsapp-signal-for-french-alternatives/
 www.yubico.com
www.yubico.com
Hey everyone, I am currently using an old(er) HYPERSECU FIDO key, USB-A with a button, and I am looking to - secure my phone as well (NFC) and, if possible - add biometric authentication to the mix. Are there good alternatives or better: upgrades to the YubiKey which do support NFC as well as biometrics and come with a USB-C? Thanks for your time 👋
cross-posted from: https://programming.dev/post/6272443 > After trying different browsers on android I found Privacy Browser to be what I need. > It have encrypted backups,Domain settings,jsless by default,Deleting all site data and Most usable UI. > Only issue is It is based on webview and I am using system default webview as my device is nonrooted so how secure is to go this way?
cross-posted from: https://programming.dev/post/6002270 > Hi, > > If you don't know how work the `chain of trust` for the http**S** > > You might want to watch this video > https://invidious.privacydev.net/watch?v=qXLD2UHq2vk > ( if you know a better one I'm all ears ) > > So in my point of view this system have some huge concerns ! > > 1. You need to relies to a preinstalled store certificate in your system or browser... > Yeah but do you know those peoples ??!! it might seem weird, but actually you should TRUST people that YOU TRUST/KNOW !! > > Here an extract from the certificate store om Firefox on Windows. > > 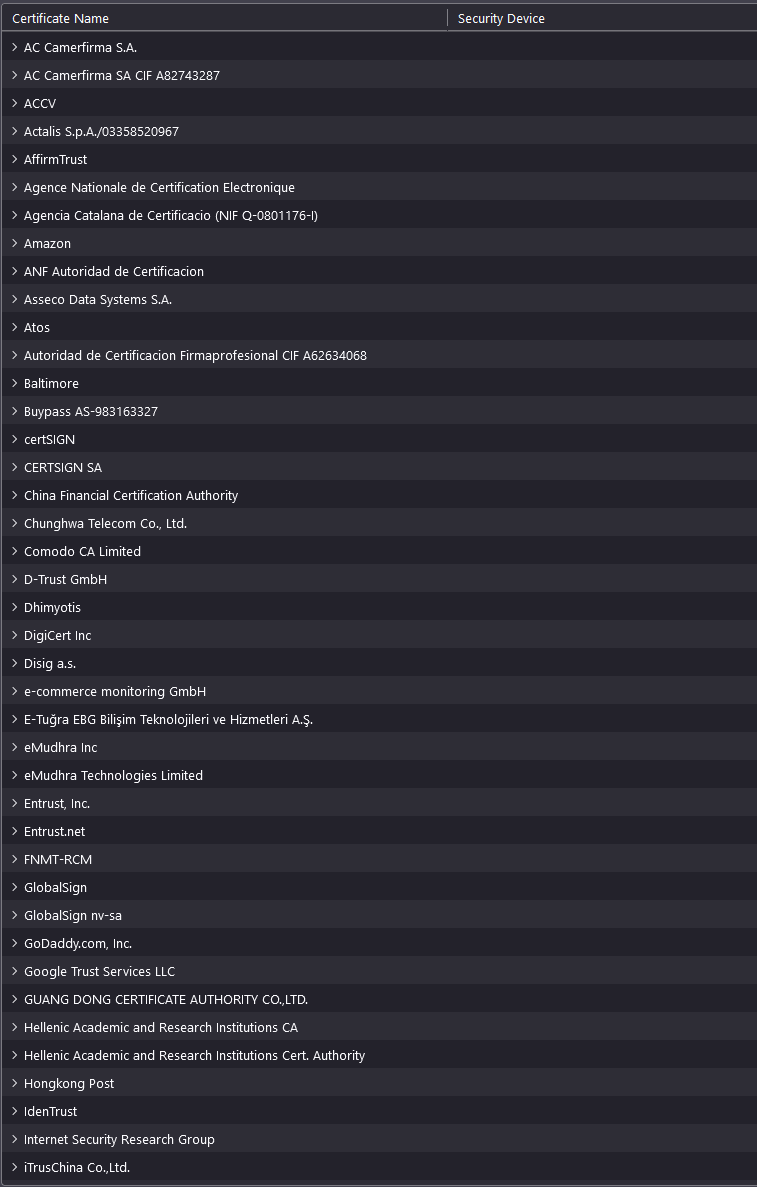 > > I do not know ( personally ) any of those COMMERCIAL company ! > > 2. Of course we could use Self-certificate but this is not protecting against Man-in-the-middle_attack . Instead of using a chain (so few 3th party involved , so increasing the attack surface ! ) why not using something simpler !? like for example > * a DNS record that hold the HASH of the public key of the certificate of the website ! > * a decentralized or federated system where the browser could check those hash ? > > > Really I don't understand why we are still using a `chain of trust` that is > 1. not trusted > 2. increase the surface of attack > 3. super complex compare to my proposals ? > > Cheers, > > > > > > ::: spoiler Why I don't use the term SSL > Because actually httpS now use TLS not anymore ssl > https://en.wikipedia.org/wiki/Transport_Layer_Security > :::
 www.eff.org
www.eff.org
With a new open letter of specialists and engineers against that hazardous project https://nce.mpi-sp.org/index.php/s/cG88cptFdaDNyRr
 write.as
write.as
Just wanted to share kind of tutorial I wrote about flashing LineageOS on old smartphones to keen them up to date 📱
 write.as
write.as
Just wanted to share an old but still relevant publication about tools to use to protect our privacy, feel free to comment and share suggestions 😁
Like Nitter and Invidious
cross-posted from: https://fedia.io/m/disabled/t/346115 > Banks have started capturing customers voice prints without consent. You call the bank and the robot’s greeting contains “your voice will be saved for verification purposes”. IIUC, these voice prints can be used artificially reconstruct your voice. So they could be exfiltrated by criminals who would then impersonate you. > > I could be wrong about impersonation potential.. just fragments of my memory from what I’ve read. In any case, I don’t like my biometrics being collected without my control. > > The countermeasure I have in mind is to call your bank using [#Teletext](https://fedia.io/tag/Teletext) (TTY). This is (was?) typically a special hardware appliance. As a linux user, TTY is what the text terminal is based on. So I have questions: > > 1. can a linux machine with a modem be used to convert a voice conversation to text? > > 2. how widespread are TTY services? Do most banks support that, or is it just a few giant banks? > > 3. if street-wise privacy enthusiasts would theoretically start using TTY in substantial numbers, would it help the deaf community by increasing demand for TTY service, thus increasing the number of businesses that support it?
From some days I have seen that piped never works and invidious works for 1/10 times.Is it due to instances are down or google is doing something. Or is it my internet issue 🥲 Is it working for others.

Title + As I dont have a G account signed in they cant track me as a person and I also turned diagnostics data sharing off. Will it be help they might track me a as person on this device.Right?? Also as to quit google I have to quit internet so will it be advantageous to do this thing.
 adguard.com
adguard.com
TL;DR > Google’s ‘ad auctions’ face a privacy challenge in the Netherlands. Google has been accused of intrusive online surveillance by more than 82,000 people who have signed up to a class action lawsuit against the tech giant in the Netherlands. > Adobe starts paying out stock contributors for helping train AI. To train Firefly, its generative AI model, the company only uses content that it has rights to through its stock image platform Adobe Stock or that is in the public domain. Adobe has now started to make good on its promise to compensate Adobe Stock creators who may lose out from the widespread adoption of AI. > UK backs down on encryption-breaking plan. The plan was to compel service providers, including messengers, to scan encrypted chats for child porn. Although the British government promised not to force companies to use unproven technology to snoop on users, it may try to enforce the so-called “spy clause” in the future if better and more secure (in the government’s eyes) technology emerges. > WhatsApp denies it will have ads. The Financial Times has reported that WhatsApp is considering inserting ads into lists of conversations with contacts in a bid to increase its revenue. A rebuttal from WhatsApp head Will Cathcart followed. “This @FT story is false. We aren’t doing this.” Still, the FT stood by their story, claiming that before it was published they had reached out to WhatsApp, and they had not denied such conversations could have taken place. Citing sources within WhatsApp, the FT then reported that another option that was being discussed is to introduce a paid ad-free version of WhatsApp. > X unveils verification system based on govt. ID. X, formerly Twitter, has begun offering its paid subscribers a new way of verification. Now, they can upload their government-issued IDs along with their selfie, and get an “ID verified” label on their profile along with “prioritized support.”
Hi I recently reviewed my Google account settings on my phone. On exploring it I found that I can Remove almost every annoying tracker,I can delete my data,Remove services,Disable Personised ads etc.After giving it 20minutes of my day I found that Google do not deserve the Hate it gets from FOSS and PRIVACY Consious people.Is there some real reason why you should not use google products for privacy or It is just everybody want to live a Hacker's life.